Identity and Access Management (IAM) solutions (providing provisioning, compliance and enforcement capabilities) are widely adopted by organizations to enable their businesses, support user management, access control, and compliance as well as deal with related security risks. However, most enterprises struggle with their IAM strategy. It is not just an IT matter.
An organization’s Identity and access management system (IAM) relies on a process of input and approval of user access to the IT system. A wrong or poor provisioning process could give more than necessary rights to users or prevent them from accessing legitimate resources. Correctly granting access rights have a significant impact on the integrity of the information system. Information held by a company’s information systems is among the most valuable assets in the company’s care and is considered a critical resource, enabling the company to achieve its objectives.
Because of the great number of business applications that an organization uses on a daily basis, user management and administration was beginning to be a rising concern and the final effect is reflected on the organization’s budget.
IT administrators’ activities include account creation, password resetting, authorization changes, job location changes, and user account deactivations. The whole administrative procedure (HR and IT) can take up to several hours, even days, depending on the number of employees who have to change their workplace (organizational unit) and the number of business applications they must use on daily basis. Daily and continuous administrative operations of HR and IT employees, organizing and distributing changes, take a significant part of HR and IT administrator’s working time.
If an employee changes their place of work within one day (due to the dynamics of business tasks) the change of information system access rights cannot be planned and implemented ahead but is carried out upon the request of the managing person. The cost of employees’ management is also reflected through the overhead expense for employees while they wait for their user account to be updated. Consequently, the employees' work will reflect on the organization's income which will be lower than the projected one.
Hence, there is a need to improve the decision process of choosing and granting access permissions to an appropriate person, as well as manage them within the organization's resources in the best cost-effective, secure and consistent way.
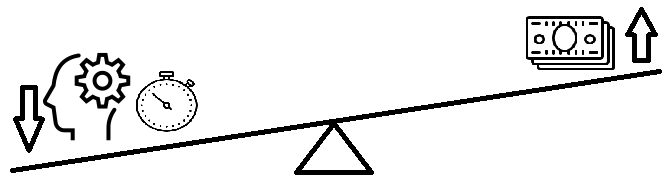
What is expected:
- improvement, which arises from a strong financial motivation
- speeding up the primary business process
- reducing the time between decisions for transferring an employee from one working place to other
- decreasing costs of administration and increasing organization revenue
For achieving expectations, few questions have to be properly answered:
- How to evaluate an employee in accordance with the required organizational needs?
- How to choose the most appropriate employee and be sure that an employee has all technical and personal preconditions fulfilled before coming to a new working place or position?

